- Last Updated: March 10, 2025
Global concerns about data privacy and cybersecurity have resulted in growing trends of in-country or on-premise data hosting. Some countries have even adopted data sovereignty and/or data localization laws.
Despite its good intentions, however, in-country data hosting doesn’t necessarily strengthen data security. Read on to learn:
1. Why hosting in-country isn’t a guarantee of safe data, and
2. How industry-leading secure survey software can protect data.
Why the interest in in-country data hosting?
As cloud hosting use has surged, so have global flows of data, leading to the rise of multinational hyperscale cloud service providers (CSPs), such as Amazon Web Services (AWS).
The data security landscape changed dramatically with the adoption of the General Data Protection Regulation (GDPR) in 2018, which introduced strict standards for processing sensitive personal data and steep fines for violators. Data privacy and cybersecurity concerns have continued to mount, exacerbated by the occurrence of large scale data breaches, such as the Capital One data breach that exposed the private data of more than 100 million consumers.
In response, some countries have adopted data sovereignty laws, which require data residency and subject data to the laws of that country. Some countries have also passed data localization laws, which require data to remain within that country. The extent of these regulations differ from one country to another and can apply to specific data types or industries. For example, in Australia, digital medical history information can’t be held or processed outside the country. Data controllers in Russia that collect personal data of Russian Federation citizens are required to carry out all handling and storing using local databases. And in Indonesia, electronic system operators who provide public services are required to have both a data center and a disaster recovery center located within Indonesia.
What does data security have to do with data storage location?
With so many data localization laws being passed, you might assume there’s a direct correlation between data security and where data is stored. But data security really depends on the means, methods, and practices of storing data, not its location. Ultimately, any Internet-connected computer server faces some level of vulnerability, regardless of where the server is located.
To help mitigate security risks, CSPs provide the architecture and operational capabilities that give users access to dynamic and responsive security practices. In fact, AWS argues that some cybersecurity risks, such as unauthorized access, are lower when using CSP services, since data residency requirements often fail to address the means attackers use most frequently to gain access (see this AWS white paper to learn more).
India, for example, which considered a data localization bill in 2019, has had numerous government database breaches, despite the fact that the compromised data was stored locally. The Aadhaar (national ID) database, Jharkhand government website, and Andhra Pradesh’s Agricultural Ministry website have all experienced data breaches and leaks that exposed sensitive data of millions of citizens. As the numbers of leaks and exposed records increase, there is no indication that the passage of a data localization bill will reduce the likelihood of these breaches in the future.
What’s our approach?
Since Dobility, Inc.’s inception, data security and privacy have been at the core of our guiding principles, and we have continued to provide industry-leading security features, including GDPR-compliant setups.
We approach the challenge of web vulnerability by giving users the highest levels of data security through end-to-end encryption, which allows an end user to generate and fully control a public-private key pair used for encrypting and decrypting sensitive data. The public key is distributed widely, and is used to encrypt the data. The private key is kept tightly controlled by the user, and is required to decrypt and read the encrypted data. Data on the server is also encrypted at the following points of the data flow process:
- Transport encryption (SSL): SSL (HTTPS) encryption protects data from being viewed by others as it travels between two parties on the Internet.
- At-rest encryption: At-rest encryption stores data separately from the encryption key necessary to read that data. This way, if the data itself is stolen or otherwise exposed, it’s safe as long as the encryption key isn’t also stolen or exposed.
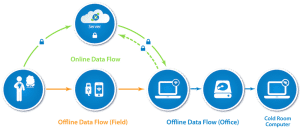
This means that user data is encrypted from the point of data collection, while in transit, and while sitting on a user server, wherever the server is located. In addition to end-to-end encryption, we can also provide the option of a fully-offline workflow for certain cases, which allows users to route their data offline and completely bypass our servers, thus avoiding any Internet-related vulnerabilities.
But suppose data residency is required?
Check the fine print
In cases where data residency is legally required, you might not have many options when it comes to using the services of firms that utilize cloud-hosting technology like SurveyCTO. However, check to confirm if the laws only apply to where readable data resides, as there is typically far less concern about encrypted (unreadable) data passing through systems in other countries. If this is the case, then our end-to-end encryption support can still be an option.
When our users use our end-to-end encryption support, the data becomes unreadable as it transits between systems. You can still ensure that readable data only resides within your country of choice by making sure that (a) data is collected and encrypted on mobile devices within the country of choice, (b) the private key needed to decrypt the data is only kept within the country of choice, and (c) once the data is encrypted within-country, the unencrypted data isn’t transmitted outside the country. To ensure even greater security for the private keys, you can keep them on cold-room computers and other fully-online, non-network-connected devices, for which we have direct support.
To fully understand any exceptions of the regulations and their applicability, make sure to conduct thorough research and have consultations with legal professionals and the appropriate authorities.
Consider all the options
Suppose your data residency requirements aren’t legally required, but instead mandated by your organization or your project? In this case, we suggest considering the reasons presented here on the limitations of in-country or on-premise data hosting, as well as their higher costs. We also encourage you to consider the solutions we can offer, like end-to-end encryption and offline workflows.
Get in touch to learn more
If you’d like to discuss these or additional options, don’t hesitate to reach out to us at info@surveycto.com. To learn more about data security with SurveyCTO, and further explore the relationship between localization and security, check out these resources:
- Product documentation
- Survey security page
- Guide to Data Security
- Protect your field research
- Baker McKenzie – Global Data Privacy & Security Handbook, 2019 Edition
- Amazon Web Services Data Residency White Paper (July 2018)
- Information Technology and Innovation Foundation (ITIF) paper – “The False Promise of Data Nationalism (December 2013)
- Hogan Lovells White Paper – Government access to Data in the Cloud (July 2012)